Table of Contents
Why you need this article
Trusted Platform Module (TPM) technology is designed to provide hardware-based, security-related functions when paired with Windows Bitlocker. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper resistant, and malicious software is unable to tamper with the security functions of the TPM. Some of the key advantages of using TPM technology are that you can:
-
Generate, store, and limit the use of cryptographic keys.
-
Use TPM technology for platform device authentication by using the TPM’s unique RSA key, which is burned into itself.
-
Help ensure platform integrity by taking and storing security measurements.
During the boot process of a system, the boot code that is loaded (including firmware and the operating system components) can be measured and recorded in the TPM. The integrity measurements can be used as evidence for how a system started and to make sure that a TPM-based key was used only when the correct software was used to boot the system.
TPM-based keys can be configured in a variety of ways. One option is to make a TPM-based key unavailable outside the TPM. This is good to mitigate phishing attacks because it prevents the key from being copied and used without the TPM. TPM-based keys can also be configured to require an authorization value to use them. If too many incorrect authorization guesses occur, the TPM will activate its dictionary attack logic and prevent further authorization value guesses.
Different versions of the TPM are defined in specifications by the Trusted Computing Group (TCG). For more information, consult the TCG Web site.
Auto activate (EasyMode)
Starting with Windows 10, the operating system automatically initializes and takes ownership of the TPM. This means that in most cases, we recommend that you avoid configuring the TPM through the TPM management console, TPM.msc. Once TPM has self configured you will have full access to the Bitlocker Manager and can enable encryption for any drive you need. There are a few exceptions, mostly related to resetting or performing a clean installation on a PC. MS is no longer actively developing TPM management console
Malware security
Antimalware software can use the boot measurements of the operating system start state to prove the integrity of a computer running Windows 10 or Windows Server 2016. These measurements include the launch of Hyper-V to test that datacenters using virtualization are not running untrusted hypervisors.
Before you Begin
- All Operating Systems configured in Legacy Boot Mode must use TPM 1.2. It is recommended the BIOS also be updated to the latest revision
- All Operating Systems configured in UEFI Boot Mode can use either TPM 1.2, or TPM 2.0. It is recommended the BIOS also be updated to the latest revision
- If a Windows 7 system is configured for UEFI Boot Mode, this patch may need to be applied in order to utilize TPM 2.0: Microsoft TPM 2.0 Patch External Link
Enabling Bitlocker
Windows BitLocker has become an increasingly popular solution for Users to secure their data. The following is how to enable and disable BitLocker using the standard methods.
This article does not discuss Group Policy changes for advanced features
Your process may vary depending on your BIOS configuration but should be fairly similar to the below
- Turn the computer on
- As the computer performs POST, press the hotkey (usually F2 or Delete) to enter the BIOS
- Once in the BIOS, locate the section that configures Security
- In the Security section, locate the TPM option
- Highlight the TPM 2.0/1.2 section on the left
- Check the TPM box on the right to switch on the TPM
- After switching the TPM on, select the option to Activate/Enable the TPM
- After the TPM has been activated and enabled, click Save changes and Exit the BIOS
- Turn the system on
-
Sign into the operating system normally
That was easy right?
Well, that's because that was the easy part. Now we need to enable Bitlocker drive encryption for a selected device.
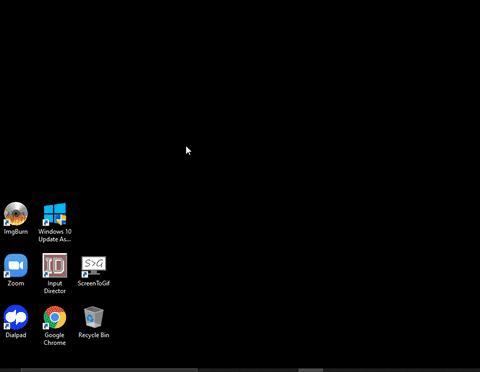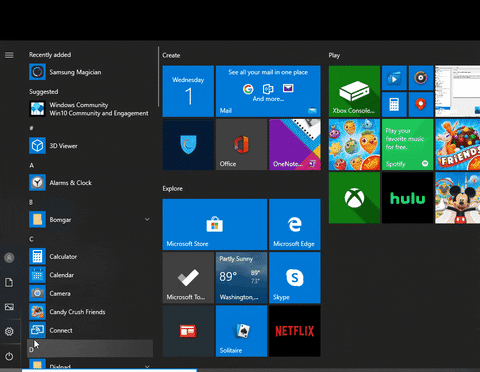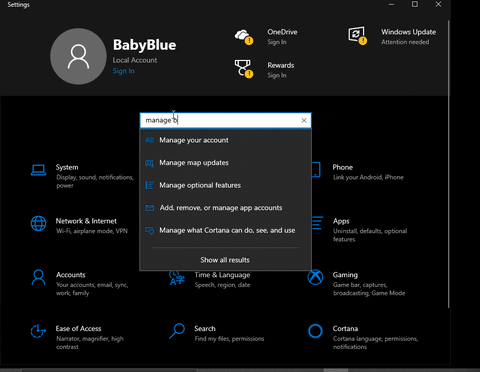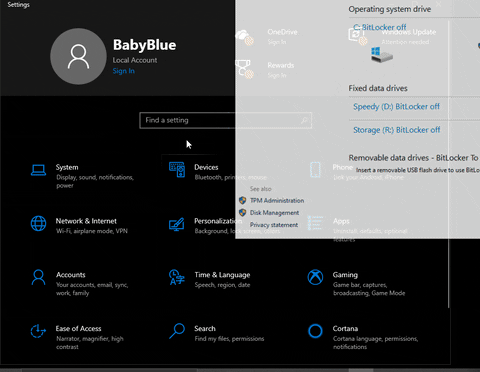
Using Settings:
- Click on the Windows Start Menu button
- Click the Settings icon
- In the search box, type Manage BitLocker
- Press Enter or click on the Manage BitLocker icon in the list
Using Start menu:
- Click on the Windows Start Menu button
- In the search box, type Manage BitLocker
- Press Enter or click on the Manage BitLocker icon in the list
Using Hard Drive menu:
- Open Computer or My Computer
- Select the C: (or Windows system) drive
- Right-click the drive that you highlighted
- Click Turn on BitLocker (NOTE: this will skip the initial BitLocker screen)
- BitLocker will go through a short initialization process
- Choose one of a few options for saving the recovery key
This key needs to be saved in a safe location. If access to the drive is ever needed, this is the recovery key that will be used to access the drive. If the key is lost, there is no option for recovering data from a locked drive and the operating system will need to be reinstalled. This key is unique for each system and will only work on the system that it was created for
- After saving the password/key file, click Next
- Select one of the volume encryption options
- Encrypt entire drive
a. This will encrypt all space on the hard drive regardless of whether or not it is used. This takes longer to process the encryption - Encrypt used space only
a. This will only encrypt space on the hard drive as it is filled with data, and leave free space unencrypted. This is preferred for basic encryption as it is faster - After selecting encryption option, click Next
- Choose the type of encryption to use if you get the encryption type selection
a. New encryption mode is the preferred method of encryption for new systems - Click Next
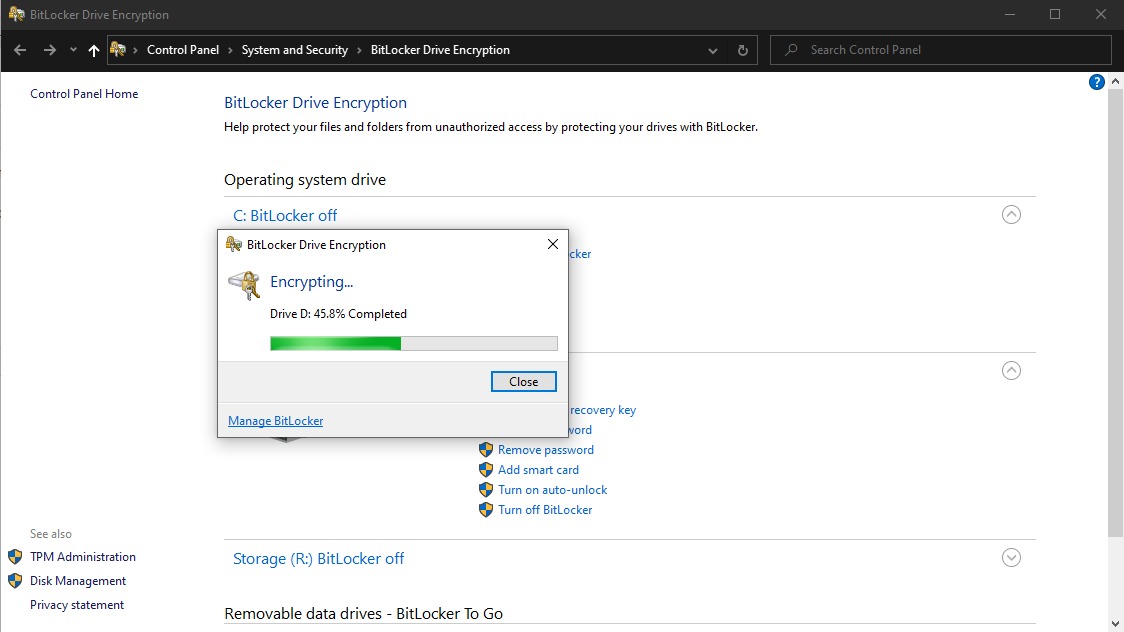
- Click Start Encrypting
The encryption process will start and depending on the size/speed of the drive being encrypted, this may take anywhere between 20 minutes and a couple hours. You can continue using your system but it's advised you don't do any major changes to files, applications or system settings
Disabling Bitlocker
For some reason or another you may wish to decrypt the drive. Just like encryption, decryption can take anywhere from 20 minutes to a couple hours, be patient.
- Open the Manage BitLocker windows with one of the above methods
- Click Turn off BitLocker
- Confirm the decision to turn off BitLocker
- Allow the system to decrypt
Conclusion
TPM and Bitlocker are a great combination providing secure booting and safe data encryption for the safest possible environment. Windows BitLocker has become an increasingly popular solution for Users to secure their data. The nature of hardware-based cryptography ensures that the information stored in hardware is better protected from external software attacks. In BitLocker, a TPM chip is used to protect the encryption keys and provide integrity authentication for a trusted boot pathway. With this article you should have all the tools needed in order to configure and manage your TPM and Bitlocker.
Need help with your Puget Systems PC?
If something is wrong with your Puget Systems PC, we are readily accessible, and our support team comes from a wide range of technological backgrounds to better assist you!
Looking for more support guides?
If you are looking for a solution to a problem you are having with your PC, we also have a number of other support guides that may be able to assist you with other issues.